The second known malware compiled to run natively on M1 Macs has now been discovered by security firm Red Canary, but the exact threat remains a mystery.
The malicious package, called "Silver Sparrow," uses the macOS Installer JavaScript API to execute suspicious commands. However, after observing the malware for over a week, neither Red Canary nor its research partners have been able to identify a definitive payload, so the exact threat posed by the malware remains a mystery. According to Red Canary, the malware is nevertheless "a pretty serious threat":
While we have not yet observed Silver Sparrow delivering additional malicious payloads, its forward-looking compatibility with the M1 chip, global reach, relatively high infection rate, and operational maturity suggest that Silver Sparrow is a fairly serious threat that is uniquely positioned to deliver a potentially high-impact payload at a moment's notice.
M1 Macs: First malware discovered only recently
According to Malwarebytes, as of February 17, Silver Sparrow has infected 29,139 macOS systems in 153 countries, including a high number in the United States, the United Kingdom, Canada, France, and Germany. Red Canary did not specify how many of these systems were M1 Macs. Noting that the "Silver Sparrow" binaries "don't seem to do much yet," Red Canary referred to them as "bystander binaries."
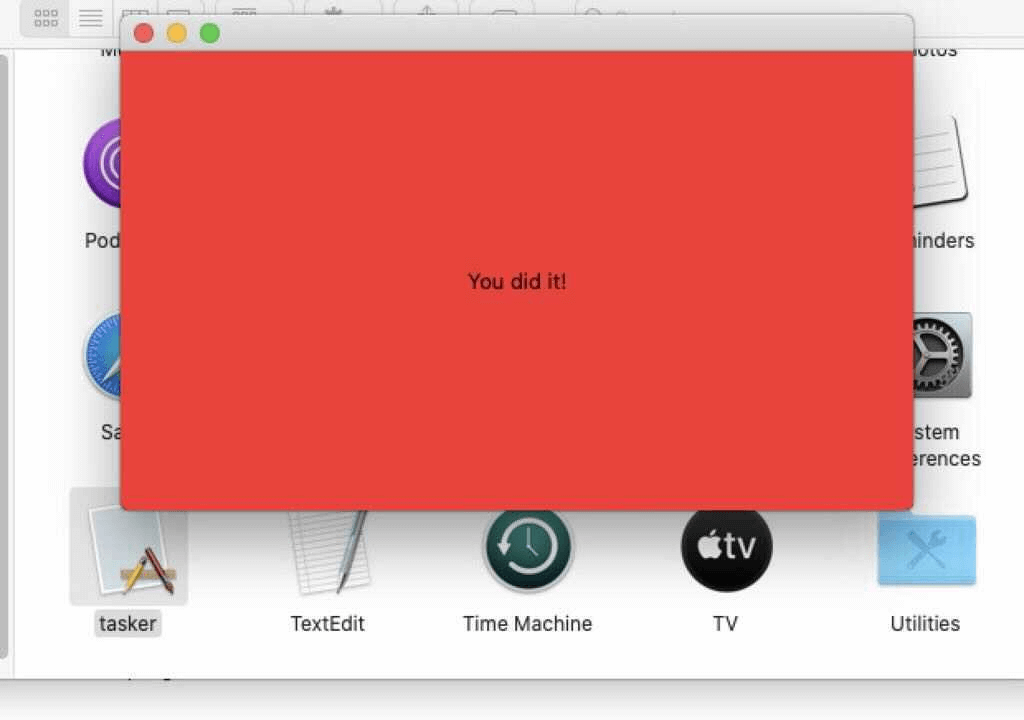
When running on Intel-based Macs, the malicious package simply displays a blank window with a “Hello, World!” message while the Apple Silicon binary leads to a red window that says “You did it!” The first malware that runs natively on M1 Macs was discovered just a few days ago. Technical details on this second malware package can be found in the blog post by Red Canary. (Photo by Ekaterina79 / Bigstockphoto)





